Short Story: Hash algorithms
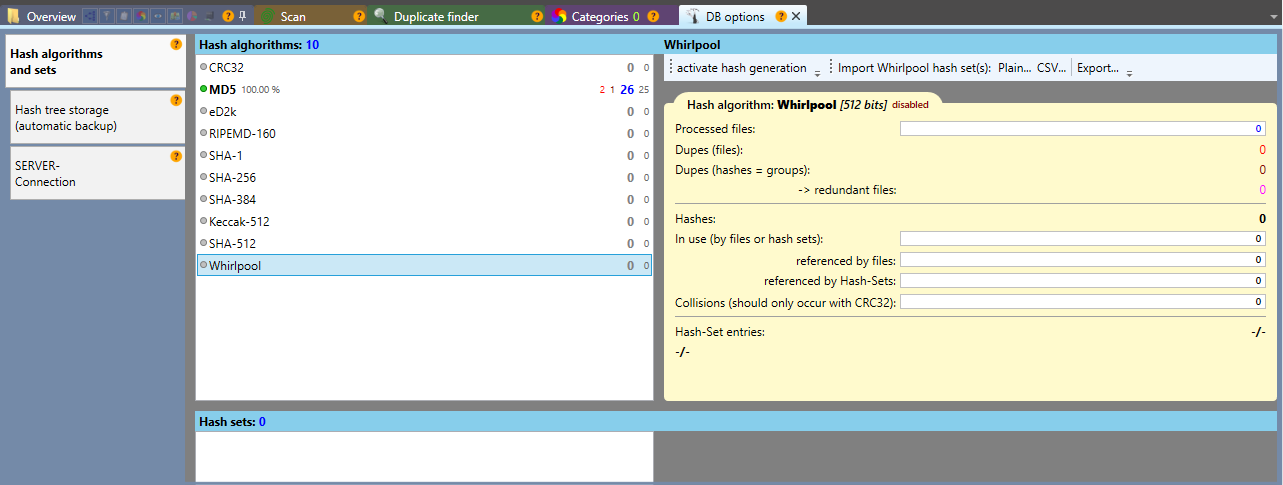
With DoublePics you have the possibility to select the desired hash algorithm BEFORE reading the files into the database. By default, MD5 and Keccak-512 are activated. You can activate other algorithms, import and export hash sets any time.
Our software is able to import hash sets from other programs. They are usually available as a CSV file (for example, X-Ways).
Hash algorithms, which are available in DoublePics:
|
Algorithm |
Description |
|
MD5 |
Message-Digest Algorithm 5 (MD5) is a widely used cryptographic hash function, that generates a 128-bit hash value from any message. This allows - for example - checking the correctness of downloads easily. |
|
Keccak-512 |
Keccak is a hash function, which was chosen as standard (Source: http://www.secupedia.info/wiki/ Keccak # ixzz48QQGVnXI) of SHA-3 (SHA Secure Hash Algorithm) by the National Institute of Standards and Technology (NIST) in October 2012. |
|
CRC32 |
The cyclic redundancy check (Engl .: cyclic redundancy check, therefore CRC) is a method for determining a check value for data to detect errors in transmission or storage. |
|
eD2k |
Many programs, such as eMule, MLDonkey and the original eDonkey2000 client can be used to find, upload and download files on the eDonkey network. The files are available on the computers of other network nodes, who can upload these files to interested parties. Files are uniquely identified by their eD2k hash. Because the hash sum remains the same, even if a file is renamed, this identification is more reliable than, for example, identification by name. |
|
RIPEMD-160 |
RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest) is a cryptographic hash function with an output of 160 bits. |
|
SHA-1 |
The term secure hash algorithm (SHA ) refers to a group of standardized cryptologic hash functions. These are used to calculate a unique check value for any digital data (messages) and are the basis for creating a digital signature. |
|
SHA-256 |
SHA-2 (secure hash algorithm ) is the generic term for the four cryptologic hash functions SHA-224, SHA-256, SHA-384 and SHA-512, which were standardized by the US NIST as the follower/child from 2001 SHA-1 (the appended number indicates the length of the hash value in bits). |
|
SHA-384 |
s. SHA-256 |
|
SHA-512 |
s. SHA-256 |
|
Whirlpool |
WHIRLPOOL is a cryptologic hash function, which is named after the whirlpool galaxy in the constellation of the Hunting Dogs. Whirlpool works with files up to a size of 2256 bits and return a hash value of 512 bits. |